Polynomial Basis Squaring
Finally have successfully found some spare time to do coding to solve this polynomial squaring:
And this is the result, x^5 + x + 1 :
Finally have successfully found some spare time to do coding to solve this polynomial squaring:
And this is the result, x^5 + x + 1 :
Cryptography is the study of mathematical techniques related to aspects of information security such as confidentiality, data integrity, entity authentication, and data origin authentication. [Handbook of Applied Cryptography – Alfred J. Menezes Paul C. van Oorschot Scott A. Vanstone]
Coding is needed for efficient reliable digital transmission and storage. [Error Control Coding – Shu Lin, Daniel J. Costello]. Coding theory is is the study of the properties of codes and their fitness for a specific application. Codes are used for data compression, cryptography, error-correction and more recently also for network coding. Codes are studied by various scientific disciplines—such as information theory, electrical engineering, mathematics, and computer science—for the purpose of designing efficient and reliable data transmission methods. This typically involves the removal of redundancy and the correction (or detection) of errors in the transmitted data. [Wikipedia]
Nggak pakai Alice & Bob?
A good article about Finite State Machine here.
Wah, itu menarik sekali untuk dibahas lho, apalagi dari sisi matematisnya, bisa sampe menggunakan teori kategori dan fungtor, coba tanya bu Intan… 🙂
A good article offering guidelines for the determination of key sizes for symmetric cryptosystems, RSA, and discrete logarithm based cryptosystems both over finite fields and over groups of elliptic curves over prime fields.
It can be downloaded here.
Aloha!
Another really good paper/report is the ECRYPT II Yearly Report on Algorithms and Keylengths. Last updated in the autumn 2011 and provides up to date key size comparisons and more.
Does anybody know comparison between (shift) register and logic gates in terms of area usage and speed?
*I know this may be technology-dependent, but some kind of rough estimate would be appreciated. Thx!*
I can’t understand the question. Shift register comprises of logic gates (i.e. when you want to build a shift register, you use logic gates as its building blocks), so why the need to compare between the two?
Care to clarify more of what do you mean by “shift register” and “logic gates”?
don’t bother, i already got the answer.
what i meant was how to count area complexity of a register or shift register in terms of logic gates (AND, XOR etc).
but thx for the response anyway 🙂
Hi… I hope eveything is ok. I was wondering, how do you solve it?
I made assumptions 🙂
port might be something you want to look into.
I know your resource site is about port but seriously.
I have seen sites like yours branch out into other
areas and its been to their benefit.
This is our poster paper to be appeared on
Pameran Hasil Penelitian
Program Riset ITB dan Program Hibah DIKTI DIPA ITB 2011
Galeri Utama Campus Centre Timur ITB
29 – 30 November 2011
Note: We do not follow the template because the posters have been printed before we found out that there is a template! 🙂
So let us present our research in contemporary design 😀
 |
| From Poster Paper Hibah DIKTI 2011 BR |
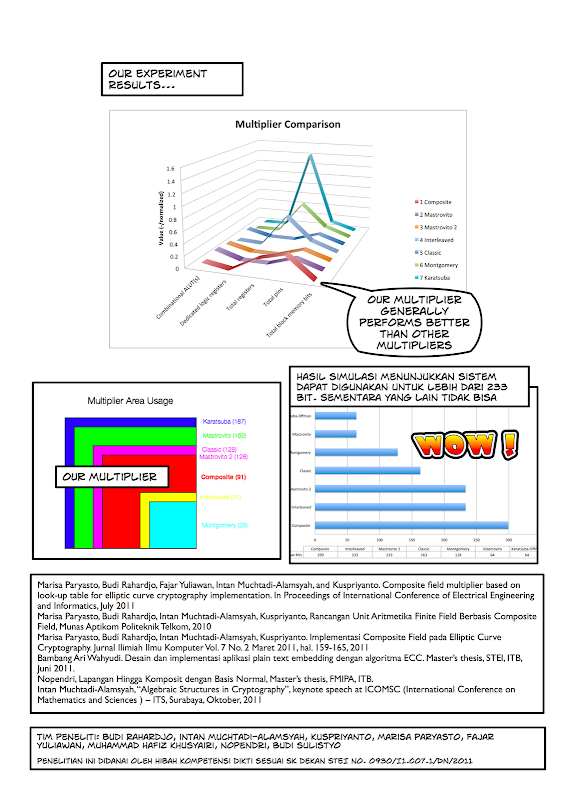 |
| From Poster Paper Hibah DIKTI 2011 BR |
[*Note: Big thanks for Fajar Yuliawan for his brilliant tutorial 😉 ]
yay! good stuff …
I took a course on Information Theory years ago when I was taking master degree and completely forgot about everything when I need to learn it quickly to use the theory to support my arguments for an cryptographic issues.
I read some books that only caused more desperation, so I decided to google some introductions about information theory, and find these brilliant video tutorials:
YouTube rocks!
youtube is a great source of useful information! high-speed bandwidth is mandatory! 🙂
cg’s hand writing …
is it decipherable? 🙂
kok mirip tulisan tangan BR ya?
mas andika: bagusan tulisan saya, hihihihhh tapi mudah2an artinya saya nantinya bisa sehebat BR dan lulus s3 *hloh
bingung bos..
This book and the software is very useful for doing experiments of encrypting using elliptic curve cryptography. I’ve been reading some thread with questions on how to change curve parameters, and here’s how:
To change the number of bits, you have to set it in field2n.h

Choose the polynomial irreducible in polymain.c

Set the message to be encrypted in elgamal.c (important note: the length of the message depends on the numbits of the curve)

rudi 9:37 pm on May 30, 2013 Permalink |
bu, akan lebih cantik kalo nulis polinomnya pake latex,

CG 11:00 am on May 31, 2013 Permalink |
iya belum sempet dirapihin 😀 biasanya saya pake latex for wordpress
Akshay 11:18 pm on July 26, 2013 Permalink |
Hey please mail me this complete C code. sorry I’m not execute this ….please help me…please ..